Locky malware report
Locky malware report
[Original post: http://www.pandasecurity.com/mediacenter/malware/cryptolocker-locky-how-it-works/]
[Original post: http://www.pandasecurity.com/mediacenter/malware/cryptolocker-locky-how-it-works/]
Intel announced four new NVMe SSDs in tandem with its Xeon E5-2600 v4 Broadwell-EP launch, and its DC P3520 and DC P3320 both come packing Intel’s new 32-layer 3D NAND. The industry is moving to 3D NAND due to the seemingly insurmountable economic challenges associated with scaling planar NAND below 10nm. Intel/Micron’s (IMFT) co-developed 3D NAND is a hotly anticipated product because it offers more density, up to 256Gb per MLC die and 384Gb per TLC die, in comparison to Samsung’s 3D V-NAND.
NAND die are stacked together into packages that support up to 16 die, and we can expect up to 512GB of storage for a single MLC NAND package and up to 768GB with TLC NAND. Samsung, and others, utilize Charge-Trap Flash (CTF) while IMFT NAND employs standard floating-gate (FG) technology. IMFT also placed most of the CMOS under the array to increase density.
Samsung was the first NAND fabricator to deliver 3D NAND to the market, but many of its competitors claim their solutions will offer better density and cost-efficiency. We are finally one step closer to finding out if those claims are true as Intel’s first 3D NAND SSDs come to market.
Intel had its new DC P3320 on display at the Broadwell-EP press briefing. The DC P3320 features the same architectural design as its Intel DC P3700 predecessor, and offers the same PCIe 3.0 x4 connection and NVMe interface.  The Intel DC P3320 comes in capacities that range from 450GB to 2TB and is available either as an Add-In Card (AIC) or in the 2.5″ form factor. The DC P3700 architecture constrains the DC P3320’s capacity because Intel’s 18-channel controller can only manage up to 2TB of addressable storage due to DRAM management limitations.
The Intel DC P3320 comes in capacities that range from 450GB to 2TB and is available either as an Add-In Card (AIC) or in the 2.5″ form factor. The DC P3700 architecture constrains the DC P3320’s capacity because Intel’s 18-channel controller can only manage up to 2TB of addressable storage due to DRAM management limitations.
The DC P3520 offers up to 365,000 random read IOPS and 22,000 random write IOPS, which is similar to the Intel DC P3500. The DC P3520 suffers a slight performance reduction due to the loss of parallelism that stems from denser 3D NAND (fewer packages). Intel did not list dedicated specifications for each capacity point, but we expect normal performance scaling based upon capacity, which means that lower-capacity models will likely offer less performance. The DC P3520 also offers up to 1,600 MBps of sequential read throughput and 1,400 MBps of sequential write speed, and a 0.3 DWPD (Drive Writes Per Day) endurance rating.
Intel indicated that it also has higher-capacity 3D TLC NAND models under development with a new architecture, which should also help boost performance.
 Intel also announced its DC P3520 SSDs, but did not share any performance data other than to note that it will be the performance-oriented model. We unearthed a document in August of last year that correctly predicted the announcement of Intel’s DC P3608 series, and it also included information on the DC P3520.
Intel also announced its DC P3520 SSDs, but did not share any performance data other than to note that it will be the performance-oriented model. We unearthed a document in August of last year that correctly predicted the announcement of Intel’s DC P3608 series, and it also included information on the DC P3520.
The slide is dated; it lists the product availability in Q4 of 2015. The other information in the document proved to be true, so we expect the data to serve as a rough guide to the DC P3520’s performance specifications. The slide indicates a top random read/write speed of 450,000/44,000 IOPS and maximum sequential throughput of 2,800/1,840 MBps.
SAS SSDs remain unchallenged in many key market segments, such as all-flash arrays, due to the dual-port interface. Dual port provides important high-availability features, such as multipath and failover, which are key requirements in mission-critical environments.
The original NVMe specification did not include dual-port functionality, but the NVMe consortium added the feature as the specification progressed. The first products with dual-port NVMe functionality are finally filtering down to the market, such as OCZ’s ZD6000, and Intel joins the ranks with its new DC D3700 and DC D3600 SSDs.
Intel’s dual-port NVMe SSDs connect via two PCIe 3.0 x2 connections. This provides the dual port connection, but also reduces performance from the top speed of 470,000/95,000 random read/write IOPS. The SSDs also provide up to 2,100/1,500 MBps of sequential read/write throughput in single port mode.
The DC D3700 and DC D3600 are only available in the 2.5″ form factor and require compatible backplanes, so they are not compatible with most systems. The DC D37600 is available in capacities of 800GB and 1.6TB and it features 10 DWPD of endurance. The low-endurance DC D3600 provides a 2 DWPD endurance rating and comes in 1TB and 2TB capacities.
The new Intel SSDs also employ several key features found in the SAS segment, such as scatter/gather lists, multiple namespaces, reservations and in-controller memory buffers. Intel indicated that its multiple namespace engine is hardware driven, which provides more performance in comparison to the software driven approaches normally used with SAS.
Intel’s 6 GBps SATA S3100 Series SSDs provide a value-centric path to SSDs by employing low-cost 16nm TLC NAND. The DC S3100 is designed specifically to serve as a low-cost HDD replacement, and many of the robust features found with the flagship-class Intel SSDs, such as power loss protection, are discarded in favor of a more palatable price point.
 The DC S3100 Series also features lower write performance than other read-centric SSDs. The S3100 offers up to 535 MBps of sequential read performance, but a mere 118 MBps of sequential write throughput. The random performance is also somewhat unbalanced at 59,000/4,700 read/write IOPS, but this is within expectations for the read-centric SSD class. The SSDs come in the familiar 2.5″ form factor in capacities of 120, 240, 480 GB and 1 TB.
The DC S3100 Series also features lower write performance than other read-centric SSDs. The S3100 offers up to 535 MBps of sequential read performance, but a mere 118 MBps of sequential write throughput. The random performance is also somewhat unbalanced at 59,000/4,700 read/write IOPS, but this is within expectations for the read-centric SSD class. The SSDs come in the familiar 2.5″ form factor in capacities of 120, 240, 480 GB and 1 TB.
The most surprising specification is the 0.1 DWPD endurance rating, which is the lowest in the market. The low endurance threshold requires the DC S3100 to be restricted to the most read-centric workloads possible, and unlike other Intel datacenter SSDs, the DC S3100 only carries a 3 year warranty.
A low price structure will be the key to the DC S3100’s success. Intel’s positioning, and the use of 16nm TLC NAND, ensures that it will be a very cost-competitive entrant, but Intel did not provide specific pricing information or release dates
Source: toms IT Pro
http://www.tomsitpro.com/articles/intel-3d-nand-dual-port-nvme-ssds,1-3217.html?_ga=1.55077422.404861095.1409680250
[Original Post: https://www.virusbulletin.com/blog/2016/02/virus-bulletin-published-first-corporate-web-filter-test-report/]
Virus Bulletin has been testing security products for more than 18 years, and in recent years, we have had many requests from product developers asking us to test their web security products. After all, whether malicious software is downloaded directly from websites or through sneaky drive-by downloads, the web remains an important infection vector.
In response to those requests we have built a new test suite to add to our existing VB100 and VBSpam tests.
The new test, called VBWeb, measures products’ ability to block malware spreading through HTTP. The test’s current focus is (corporate) gateway solutions that run on the network as an implicit or explicit proxy. We are looking to extend the test in the future to on-desktop and in-browser solutions.

Given how quickly web-based threats change, and given how many of them actively attempt to frustrate researchers (something we have also frequently run into), building a web security product is not a trivial task, and submitting such a product to a public test isn’t something vendors do without serious consideration.
In this test, while there were several participants, the developers of Fortinet‘s FortiGuard appliance were alone in agreeing for their product to be tested publicly. Their confidence in the product proved to be well founded: it blocked all but a few out of hundreds of malicious downloads, as well as a significant number of live exploit-kits.
Indeed, with an 83% catch rate – well over the 70% threshold required for VBWeb certification – FortiGuard is a clear and deserved winner of the very first VBWeb award.
You can read the full report here in HTML format, or download it here as a PDF. The report describes the testing methodology in full detail.
From now on, VBWeb will be run every second month. Product developers who are interested in submitting a product for the test (publicly or privately) can contact Virus Bulletin‘s Editor Martijn Grooten at martijn.grooten@virusbtn.com.
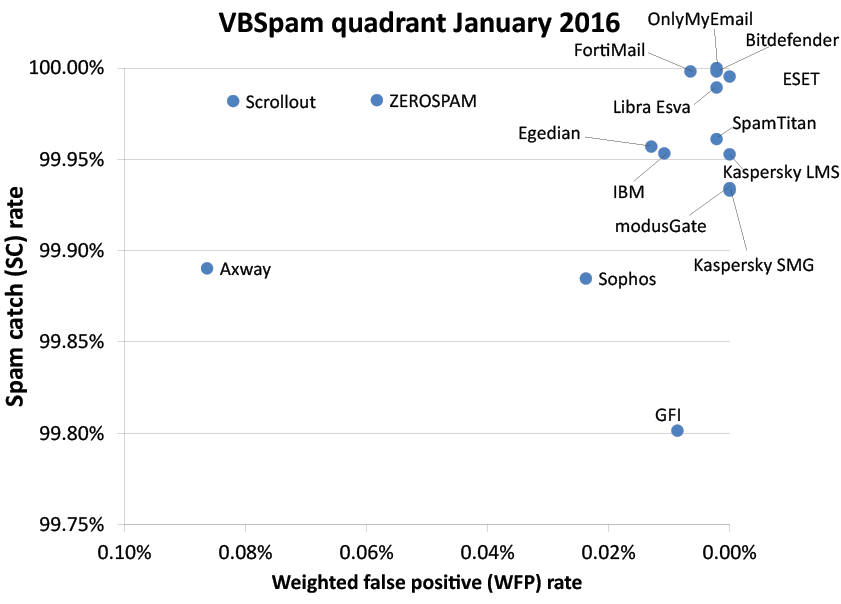
Of course, HTTP isn’t the only infection vector systems administrators have to be worried about. But in the case of email, there is good news: all 16 participating full solutions achieved certification in the latest VBSpam test, which saw record catch rates. Ten products even achieved a VBSpam+ award, after blocking more than 99.5% of spam while also avoiding false positives.
You can read the full report here in HTML format, or download it here as a PDF.
IBM researchers, Tayfun Gokmen and Yurii Vlasov, unveiled a paper in which they invented the concept for a new chip called a Resistive Processing Unit (RPU) that can accelerate Deep Neural Networks training by up to 30,000x compared to conventional CPUs.
A Deep Neural Network (DNN) is an artificial neural network with multiple hidden layers that can be trained in an unsupervised or supervised way, resulting in machine learning (or artificial intelligence) that can “learn” on its own.
This is similar to what Google’s AlphaGo AI has been using to learn playing Go. AlphaGo used a combination of a search-tree algorithm and two deep neural networks with multiple layers of millions of neuron-like connections. One, called the “policy network,” would calculate which move has the highest chance of helping the AI win the game, and another one, called the “value network,” would estimate how far it needs to predict the outcome of a move before it has a high enough chance to win in a localized battle.
Many machine learning researchers have begun focusing on deep neural networks because of their promising potential. However, even Google’s AlphaGo still needed thousands of chips to achieve its level of intelligence. IBM researchers are now working to power that level of intelligence with a single chip, which means thousands of them put together could lead to even more breakthroughs in AI capabilities in the future.
“A system consisted of a cluster of RPU accelerators will be able to tackle Big Data problems with trillions of parameters that is impossible to address today like, for example, natural speech recognition and translation between all world languages, real-time analytics on large streams of business and scientific data, integration and analysis of multimodal sensory data flows from massive number of IoT (Internet of Things) sensors,” noted the researchers in their paper.
The authors talked about how in the past couple of decades, machine learning has benefited from the adoption of GPUs, FPGAs, and even ASICs that aim to accelerate it. However, they believe further acceleration is possible by utilizing the locality and parallelism of the algorithms. To do this, the team has borrowed concepts from next-generation non-volatile memory (NVM) technologies such as phase change memory (PCM) and resistive random access memory (RRAM).
The acceleration for Deep Neural Networks that is achieved from this type of memory alone reportedly ranges from 27x to 2,140x. However, the researchers believe the acceleration could be further increased if some of the constraints in how NVM cells are designed were removed. If they could design a new chip based on non-volatile memory, but with their own specifications, the researchers believe the acceleration could be improved by 30,000x.
“We propose and analyze a concept of Resistive Processing Unit (RPU) devices that can simultaneously store and process weights and are potentially scalable to billions of nodes with foundry CMOS technologies. Our estimates indicate that acceleration factors close to 30,000 are achievable on a single chip with realistic power and area constraints,” said the researchers.
As this sort of chip is only in the research phase, and because regular non-volatile memory hasn’t reached the mainstream market yet, it’s probably going to be a few years before we begin to see something like it on the market. However, the research seems promising, and it may raise the attention of companies such as Google, which wants to accelerate its AI research as much as possible. IBM itself is also interested in solving Big Data challenges in healthcare and other domains so the company’s own businesses should benefit from this research in the future.
Source: Toms hardware
http://www.tomshardware.com/news/ibm-chip-30000x-ai-speedup,31484.html

The complaints about MacKeeper are all over the shop: It’s a virus. It holds your machine hostage until you pay up. It can’t be completely removed if you decide to delete it. Instead of speeding up your computer, it slows it down. It erases your hard drive, deletes photos, and disappears documents. There are protests about MacKeeper’s annual subscription fees. Zeobit is slammed for seedy marketing tactics. It runs pop-under ads, plants sock-puppet reviews and encourages sleazy affiliate sites, critics say.
But what’s really strange is that MacKeeper has been almost universally praised by professional reviewers. All week I’ve been checking out reviews on the Web and I can’t find a bad one.
All the reviews praise the software for being well designed and easy to use. Macworld magazinecalls it “a gem.” TUAW gives it a favorable review. Dave Hamilton of Backbeat Media, a Mac industry veteran, recently talked it up at Macworld Expo. None of the professional reviewers complain of slowed-down machines or deleted data.
Given the comments on our deals post, I started researching Zeobit and MacKeeper. (Our deals, by the way, are determined by our partners, StackSocial.) I was alarmed that Cult of Mac might be promoting malware, but quickly became curious why such well-reviewed software gets such bad reviews from users. I reached out to Zeobit and Symantec, which publishes anti-virus and security software under the Norton brand.
Jeremiah Fowler, Zeobit’s PR Director, said Mac security companies get a bad rap because Apple users generally believe there is no need for anti-virus products. The Mac is immune to malware, according to users, and therefore any company that sells security software is by definition a scam.
“I personally believe it is just the nature of the business in the age of internet trolling and it is so easy for anyone with too much time on their hands to trash businesses or products online anonymously and with no repercussions,” he wrote in an email. “We have 150 employees and really do care about the products we make and the people who use them.”
Symantec’s Mac Product Manager, Mike Romo, said the same thing: the company is criticized for the very idea of selling security products for the Mac. Users think they are utterly unnecessary and ruin the frictionless experience of OS X. “It’s a great community but it’s very vocal,” Romo said in a telephone interview. “It would be a lot easier to make a painting program or something.”
Romo, who describes himself as a hard-core Mac user, said users voice similar complaints to those heard by Zeobit. However, he says the criticisms are like an urban myth — they are based on rumor and hearsay. “I ask them if they have used our product,” he said. “Ninety-nine percent of the time, they have not.”
“We’re used to getting the hate,” he added,” but we love and believe in what we are doing.”
Zeobit’s Fowler said the company has become a “forum punching bag” thanks to four things: a negative PR campaign from a rival company; Zeobit’s aggressive advertising tactics; out-of-control affiliates; and confusion among users between MacKeeper (legit software) and MacDefender (a Trojan). (See Fowler’s full note below.)
While looking into Zeobit last week, I came to some of these same conclusions myself. Zeobit has earned a lot of notoriety for its advertising practices. It’s a very active and aggressive marketer. It runs online ads everywhere, including sneaky pop-unders. It parades scantily-clad booth babes at Macworld. The company also runs an affiliate program that appears to be widely abused. According to Fowler, the sleaziest Zeobit marketing comes from third parties that it has no control over.
Some of the wilder accusations — that Zeobit is a hacker outfit that makes an insidious virus — are way off. The company was one of the sponsors of Macworld, which is as mainstream as a trade show gets. Apple sells a lite version of MacKeeper called 911 Bundle through the official Mac App Store, which is carefully vetted for malware.
Likewise, Cult of Mac does not offer malware through our Deals program. As far as I can tell, MacKeeper is a legit piece of software run by a company whose sales and marketing tactics rub many in the Mac community the wrong way. It may not be for everyone, but MacKeeper is not a virus or a scam. And right now, it’s 50% off ;-).
Here’s is MacKeeper’s PR Director Jeremiah Fowler’s full statement to Cult of Mac:
++
Hello Leander,
Thanks for your message and I will be happy to contact a 3rd party user about speaking with you. With the bad comments we are all too aware of them and they actually fall under a few different categories of why people are anti-MacKeeper. Just to give you an idea of what we face on a daily basis, here is a short breakdown of the key reasons people complain.
Also, as a general rule look at some of the other companies who are in the business of Mac security and see the search results for example if you search Google for norton+mac+sucks you will get about 18,700,000 results… We know that Norton is not a bad company, right? You may not like them or their products but you know they are not scammers and their software is not malware, but the internet is loaded with thousands of results saying the opposite. The results are the almost the same for nearly every industry leading software that offers Mac Security. I personally believe it is just the nature of the business in the age of “Internet Trolling” and it is so easy for anyone with too much time on their hands to trash businesses or products online anonymously and with no repercussions. We have 150 employees and really do care about the products we make and the people who use them. You can see some of our real customers and industry professionals talking about MacKeeper on our YouTube Channel here.
Reasons:
We were the victim of a massive black PR campaign by a small competitor who is now cloning our apps one at a time:
The story was featured here: EXCLUSIVE: MacKeeper Says “Unethical Competitor Trying to Tarnish Our Reputation”
These guys were running Google ads saying we were scammers selling malware and anything else bad that they could create, we got those ads suspended for violating Google’s ad terms and the fine folks at Google 100% confirmed exactly who was the competitor running them against us. So, what this did was trigger a kind of “Band Wagon Effect” of others who were like “Yea we hate them”. They actually hired people in their office who used forum spam, link spam, blogs and paid articles to slander us in ways we are still feeling a year later. As mentioned in the article instead of wasting our time and energy doing the same back to them, we have decided to focus only on making our product better and listening to our real users. We think that focusing on our products and service instead of forum trolls, is a far better business model in the long run.
Legitimate Mac Users who are annoyed or tired of our advertising campaigns or partner’s campaigns. Do we advertise? Yes! Do we advertise aggressively, I would not like to use that term but we do have a massive advertising presence online! We have had 15,000,000 downloads of MacKeeper and have a less than 3% refund rate. The reality is that many people are truly happy with the product even if they hate the advertising (and unfortunately some do). The bad part is some people take their hatred for advertising to a level where they dedicate hours of their lives to making MacKeeper a “Forum Punching Bag”… In a perfect world there would be no advertisements on radio, TV, billboards or the internet, but this is not a reality. As long as there are ads, there will be people who hate them.
We believe that we have a great product and we want people to know about it and the only way to do this is to explore every medium of advertisement. It is like investing everything in to a great restaurant and hiring the best chefs, buying the best food only to hide the location somewhere in the woods and then tell no one about it. Then wondering why no one comes to your restaurant? We are discussing phasing out our ads and trying to please the vocal minority, but we realize that pleasing everyone is impossible.
We have suspended many affiliate accounts for violating our terms and while these guys were trying to make a fast income they were trashing our image in the process. The problem is that although we suspend their account, the effects of their actions fall on us and cause serious harm to our reputation in the process.
In May 2nd 2011, a rogue security program called “MacDefender” (also known as Mac Protector, Mac Security, Mac Guard, and Mac Shield) was identified. This fake antivirus software had nothing to do with nor had any affiliation with MacKeeper or ZeoBit LLC, but used a similar name to MacKeeper. This also caused a lot of confusion and created a huge problem of Mac Users who were not familiar with MacKeeper.
Please let me know if you have any additional questions and I will be happy to help you.
Also please check out some of the real users on our YouTube Channel.http://www.youtube.com/MacKeeperTV
While SMS has been declared dead many times, the service remains frequently used – and abused.
In a paper presented at VB2015 in Prague, Adaptive Mobile researcher Cathal Mc Daid looked at fraudulent SMS campaigns, in particular those targeting banking users in North America.
He showed how these campaigns tend to target specific banks and specific regions, especially those on the East Coast, and also looked at how, similar to what we have long seen in email spam, the messages keep changing in subtle ways, to stay one step ahead of detection.
You can read his paper “Mobile Banking Fraud via SMS in North America: Who’s Doing it and How” here in HTML format or hereas a PDF, and find the video on our YouTube channel, or embedded below.
Are you interested in presenting your research at the upcoming Virus Bulletin conference (VB2016), in Denver 5-7 October 2016? Thecall for papers is now open.
Posted by Martijn Grooten on Mar 2, 2016
Troy Hunt, a security researcher uncovered a vulnerability in the NissanConnect app, which can allow attackers to connect to a car if they know their car’s ID number. After that, they can hijack the car’s air conditioning and heating systems. The fault lies in the complete lack of authentication for the application that enhances the car’s dashboard with Internet-connected features.
The vehicle identification number (VIN), which is written on each Nissan Leaf’s windshield, can be copied by anyone that passes by that car. However, the VIN is composed of characters that refer to the brand, make of car, and the country where it was manufactured. Only the last five digits vary between different Leaf cars in the same region, so someone could just build a script to attack all of the Nissan Leafs in a given region.
“There’s nothing to stop someone from scripting a process that goes through every 100,000 possible cars and tries and turn the air conditioning on in every one,” said Troy Hunt. “They would then get a response that would confirm which vehicles exist.”
The security expert also noted that attackers don’t even need to use the NissanConnect app, because they can deliver the attack through a web browser by spoofing the app. The Australia-based researcher tested this on a Nissan owned by his friend Scott Helme, who lives in the U.K.
“As I was talking to Troy on Skype, he pasted the web address into his browser and then maybe 10 seconds later I heard an internal beep in the car,” said Helme. “The heated seat then turned on, the heated steering wheel turned on. And I could hear the fans spin up and the air-conditioning unit turn on.”
Hunt said that the test didn’t work when the car was in motion, but it did show the owner’s registered username, which could help reveal their identity. Times and distances of recent journeys were also revealed.
When Helme unregistered the app, Hunt’s attack no longer worked. This is why Hunt suggested that this vulnerability could be easily fixed if the company disables the ConnectNissan service.
The researcher said that although this isn’t a life-threatening attack, it could be used in ways that could put the cars’ owners in danger. For instance, if the attackers hijack the car this way, they could see over the course of a week where the driver goes to work, and then they could drain the car’s battery to make it so the driver can’t get back home.
Hunt alerted Nissan about the flaw a month ago, but so far he hasn’t gotten a proper response about it, so he decided to make it public to force the company to fix the issue. He said he has already seen some Canadian Leaf owners share information about this vulnerability online, so the issue is already out there, whether he would’ve kept it a secret or not.
This is why sometimes security researchers, who discover vulnerabilities in some products, can’t wait for the companies to provide a fix if it takes longer than a few months and it looks like they are dragging their feet. Usually, it’s not just one person that finds that vulnerability, but many others, who exploit it for their own purposes; therefore allowing the company to drag the process of fixing the issue doesn’t mean that others aren’t taking advantage of that vulnerability during that time.
This case also shows that although most car manufacturers are rapidly trying to build connected cars, electric vehicles that are almost completely controlled by software, and even self-driving cars, where the danger of software insecurity is even bigger, they aren’t taking security all that seriously.
Software security in these modern cars should be treated at least as seriously, if not more so (because software security is so hard), as any other safety mechanism in a car. A software feature that could slightly increase the owner’s convenience in using such a modern car could be turned into something that’s used to crash that car. That’s why car manufacturers need to think very carefully about each new software feature that they add to their cars, and it always needs to be written in a context of high security.
Source: Toms Hardware
http://www.tomshardware.com/news/nissan-leaf-hacked-web-link,31275.html
Kingston’s $4.25 million acquisition of the IronKey assets from Imation was a rare occurrence, as the fairly conservative company is not known for merger and acquisition activity. Kingston tends to favor internal development of new technology and products, and the company has met with resounding success in its efforts thus far. However, Kingston decided to procure the USB technology and assets when the IronKey portion of the Imation portfolio became available, but sold the IronKey external HDD business. This choice makes sense, as Kingston is a company built upon its core flash competency. 
Kingston offered its own FIPS 140-2 Level 3 (the highest level) encrypted USB products for 12 years, but its encrypted USB products appealed more to the general client market and tended to be pricey. Kingston did not attain the traction that the IronKey brand gained with lucrative business and government customers. Kingston will integrate the full breadth of IronKey products into its portfolio, and the company will offer all of the existing and future IronKey products under “Kingston IronKey” branding.
Kingston bucks the long-held, and mostly accurate, industry predictions that indicate fab-less SSD vendors will fall to the wayside. It is incredibly hard to compete with firms that produce their own NAND, but according to the Trendfocus CQ2015 Total SSD Market report, Kingston still holds a commanding presence in the global SSD market. Surprisingly, its 10.1% share of the total global SSD market outweighs several of its fab-enabled competitors, such as Intel, Micron, Toshiba, SK Hynix and SanDisk.
Kingston innovates by staying on the cutting edge of NAND technology – it procures NAND wafers and processes and packages the raw NAND into packages, thus ensuring cost efficiency that allows it to compete with the fabs. NAND fabs are beholden to their own NAND, but Kingston has the flexibility of procuring NAND from a number of sources. This helps ensure that it has access to the best performance and price for each successive NAND generation.
Imation built its IronKey products on an older hardware platform. In the encryption market, reliability and security typically outweigh performance and cost considerations. In fact, Imation did not actually produce its own products; it sub-contracted that aspect of its business out to third parties. Kingston’s extensive experience and technology will allow it to upgrade the current IronKey products to new and more cost–effective controllers and NAND. This will allow Kingston to offer the IronKey products at lower prices, which should help foster wider adoption in diversified market segments beyond the core Imation business and government contracts.
The majority of Kingston’s purchase centers on the IronKey IP. Imation had no dedicated production facilities due to its third-party production model. Kingston will continue to use the third-party manufacturing for a short time as it spins up its own facilities. The manufacturing transition will obviously be a top priority, as it will lower cost and allow Kingston more control of the supply chain.
The hardest part of any M&A activity always centers on the successful melding of the different cultures inside each respective company, but Imation had laid off a number of IronKey staff in December of 2015, and it did not keep any full time employees. This unfortunate fact should help Kingston integrate the two companies quickly.
DataLocker procured the IronKey management service assets, which is an integral portion of the IronKey product portfolio. Kingston and DataLocker had an extensive working relationship in the past, and Kingston signed a three-year contract with the company to provide the software piece of the puzzle. This move makes sense, as Kingston wishes to focus on its own core capabilities, thus leaving the software piece to the software company. Kingston also divested the IronKey HDD assets to DataLocker.
There was a thirty-day transition period signed into the Kingston/IronKey contract that has already expired. Kingston is now shipping the full breadth of IronKey products under its own branding. Kingston will maintain its encrypted DataTraveler products for customers who do not require the extra brick wall of FIPS 140-2 level encryption.
Melding the Imation IronKey technology portfolio with Kingston’s deep NAND experience, design expertise and manufacturing prowess should be a win for the consumer. Imation had a reputation for high-priced products, which Kingston’s scale should help remedy.
Kingston plans to extend its full global sales and support mechanism to all existing IronKey customers, and the promise of newer and more cost-effective solutions will bolster the long-term prospects for Kingston’s security-conscious USB products.
Source: Toms IT Pro
http://www.tomsitpro.com/articles/kingston-ironkey-imation-usb-encryption,1-3182.html
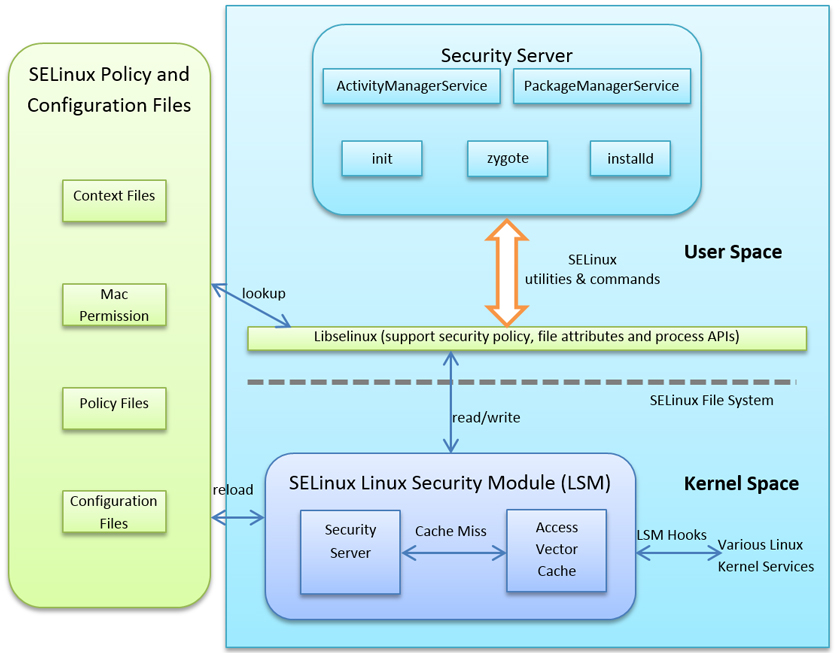
Google‘s Android operating system may have a bit of a bad reputation when it comes to security, but it’s worth noting that recent versions of the operating system have been hardened a lot.
In a paper presented at VB2015, Sophos researchers Rowland Yu and William Lee look at two recent security enhancements, Security Enhancements for Android (SEAndroid) and containerization, and ask whether they will be able to stop future malware targeting Android. Based on how existing Android malware gets onto the operating system, they conclude that these enhancements won’t be sufficient to keep either current or future malware out.
You can read their paper “Will Android Trojans, Worms or Rootkits Survive in SEAndroid and Containerization?” here in HTML format or here as a PDF, and find the video on our YouTube channel, or embedded below.
If you’re interested in Android malware, don’t forget to read Rowland Yu’s VB2014 paper “Android packers: facing the challenges, building solutions”, or watch him discuss Android malware at RSA next month.
[]
Original Post: https://www.virusbulletin.com/blog/2016/02/vb2015-paper-will-android-trojans-worms-or-rootkits-survive-seandroid-and-containerization/
NXP announced the LS1012A processor, which the company claimed is the smallest and lowest power 64-bit chip that comes with multiple built-in hardware security features.
The LS1012A chip is powered by a single-core 64-bit Cortex-A53 CPU, which makes it one of the most powerful IoT-focused chips around, and yet the chip is contained in that small 9.6 x 9.6 mm package.
NXP said that the LS1012A is the first chip small enough to be integrated directly onto the printed circuit board of an HDD, which means it enables the existence of “Ethernet drives” that have the same form factor as existing HDDs. These sort of drives can be used in data centers that employ
object-based file architectures that work across networks of intelligent HDDs.
At 2,000 CoreMark of performance, the chip consumes about 1 W of power. It has a Packet Forwarding Engine for acceleration of IP packet processing to reduce CPU load and power consumption. It also includes support for peripherals such as USB 3.0, PCIe, 2.5 Gbps Ethernet, and SATA3.
“The groundbreaking combination of low power, tiny footprint and networking-grade performance of NXP’s LS1012 processor is ideal for consumer, networking and Internet of Things applications alike,” said Tareq Bustami, senior vice president and general manager of NXP’s Digital Networking division.
“This unique blend of capabilities unleashes embedded systems designers and developers to imagine and create radically innovative end-products across a broad spectrum of high-growth markets,” he added.
One of the main selling points of the chip is its security features, which include built-in hardware root of trust, crypto acceleration, secure debug, secure manufacturing (the firmware is protected against malicious manufacturing employees), and an ARM TrustZone, where the cryptographic master keys are stored.
The software development kit supports Linux. NXP also offers “application solution kits” based on OpenWrt, the popular open source Linux-based embedded operating system. It’s typically used for routers, but it can also be used for IoT gateways and networked storage. The company said it supports other third-party operating systems, tools and development boards, too.
The development tools will include the full software development kit with Yocto support, CodeWarrior for the 64-bit ARMv8 toolchain, and a reference development board. NXP’s LS1012A chip will be available in April 2016, but you can order it now.
Source:
http://www.tomshardware.com/news/nxp-ls1012a-smallest-iot-chip,31249.html
Questions, issues or concerns? I'd love to help you!